Why AI Governance Matters: A Guide for Businesses and Municipalities
Why AI Governance Matters: A Guide for Businesses and Municipalities
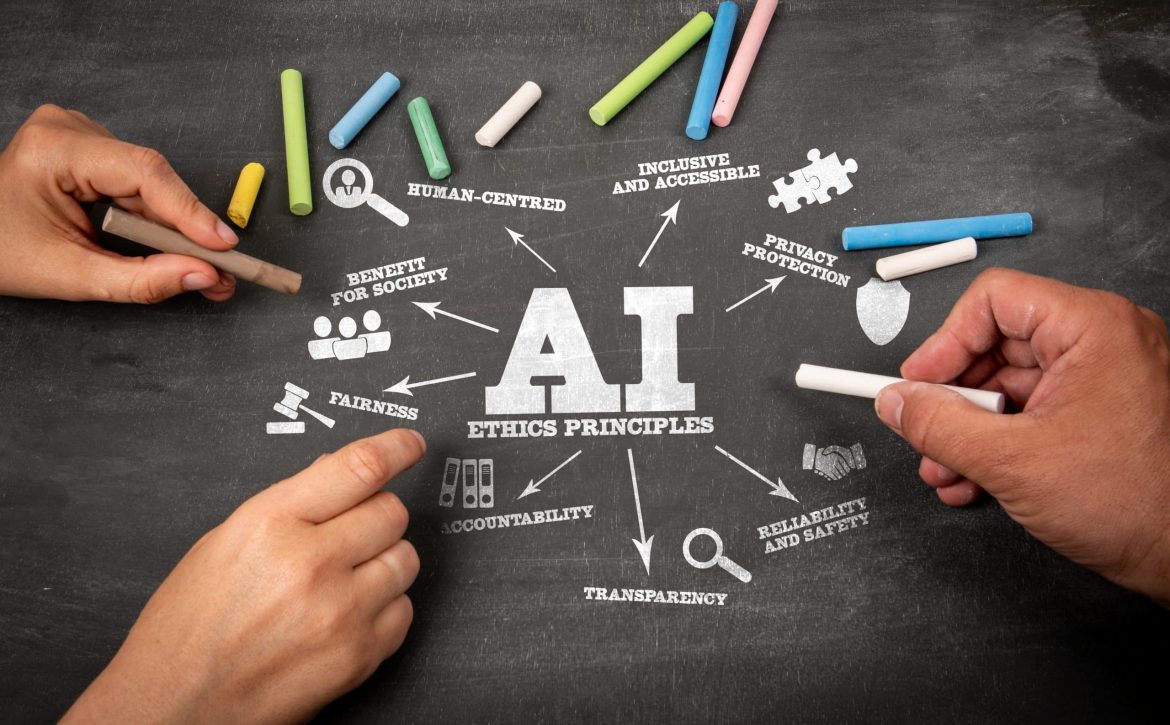
Why AI Governance is Important
Artificial intelligence (AI) is rapidly transforming our world, offering incredible potential for innovation and progress. However, with this power comes a responsibility to ensure that AI is developed and used in an ethical and responsible manner in the early days of this IT revolution. This is where AI governance comes into the mix….
What is AI Governance?
AI governance refers to the processes, policies, and frameworks that guide the development and deployment of AI systems. It encompasses everything from establishing ethical guidelines for AI development to ensuring transparency and accountability in AI decision-making.
Why is AI Governance Important?
AI governance is critical for several reasons:
- Ethical Considerations: AI systems can make decisions that have significant real-world consequences. AI governance helps ensure that these decisions are aligned with human values and avoid unintended harm.
- Bias and Discrimination: AI systems can perpetuate and even amplify existing biases in data and algorithms. AI governance helps mitigate these risks and promote fairness and inclusivity.
- Transparency and Accountability: It’s essential to understand how AI systems work and how they arrive at their decisions. AI governance promotes transparency and accountability, ensuring that AI systems are not used as uncheck resources.
- Security and Privacy: AI systems often handle sensitive data. AI governance helps protect this data and prevent unauthorized access or misuse.
- Public Trust: AI governance helps build public trust in AI technologies by demonstrating that they are developed and used responsibly.
How Businesses and Local Municipalities Can Implement AI Governance
Businesses and local municipalities can take several steps to implement effective AI governance:
- Develop Clear AI Policies: Establish clear policies that outline the ethical principles and guidelines for AI development and use.
- Create Multidisciplinary Teams: Assemble teams with diverse expertise, including AI specialists, ethicists, and legal experts, to oversee AI projects.
- Prioritize Data Quality and Privacy: Ensure that data used to train and operate AI systems is accurate, unbiased, and protected.
- Conduct Regular AI Audits: Regularly assess AI systems for bias, security vulnerabilities, and adherence to ethical guidelines.
- Foster Collaboration and Knowledge Sharing: Engage with other organizations to learn from their experiences and best practices in AI governance.
By prioritizing AI governance, businesses and local municipalities can harness the benefits of AI while mitigating the risks and ensuring that AI serves the best interests of society. AI technology is rapidly integrating itself within the IT landscape and it is truly in the best interests of organizations to stay ahead and adapt to the inevitable challenges that will impact businesses and governments alike.
Prepared to take the first steps towards AI Governance? Eaton & Associates is ready to guide your organization through the latest best practices and roadmap a plan that balances your AI needs while maximizing practical approaches to AI governance.
AI Responsibility Advocates:
The Future Society: A nonprofit organization focused on aligning AI through better governance. The Future Society